Are car makers rushing into the connected-vehicle era without properly evaluating the risks?
That’s the concern raised by two computer and network security researchers from England who provided a comprehensive overview of cybersecurity in modern cars, and the threats posed by increased connectivity.
With the introduction of telematics, vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communications, and the integration of smartphones and Bluetooth devices, connected vehicles can create their own ecosystems that are part of a larger, fully connected world. Like every other Internet of Things application, though, the software that makes these vehicles so advanced, also makes them vulnerable to cyberattacks.
“In general, car manufacturers are rushing into integrating communications technologies with their cutting-edge cars, before there is rigorous testing in place,” said researcher Mahmoud Hashem Eiza, whose article “Driving with Sharks: Rethinking Connected Vehicles with Vehicle Cybersecurity” was published in IEEE Vehicular Technology Magazine. “Damages of vehicle cyberattacks can be severe and irreversible as it concerns human lives. Hence, this subject area still needs more investigation and research efforts from academia, auto industry and governmental bodies.”
Numerous vehicles have been remotely hacked in recent years. These attacks have drained batteries, left cars without alarm systems, and have even placed unpiloted cars on the highway. And unlike a car thief, hackers only need to be in communication range (which can be several miles) of the targeted vehicle to gain access. That is a serious and potentially life-threatening issue.
Here’s a quick look at how modern vehicles can be hacked:
The figure below details potential attack points for the in-vehicle network architecture. The network contains many electronic subsystems, each containing many electronic control units. Each electronic control unit is in charge of a specific function in the vehicle. For example, the units that control the airbag deployment and the antilock braking system (ABS) are found in the vehicle safety subsystem, while the units that provide engine control and suspension control are found in the powertrain subsystem.
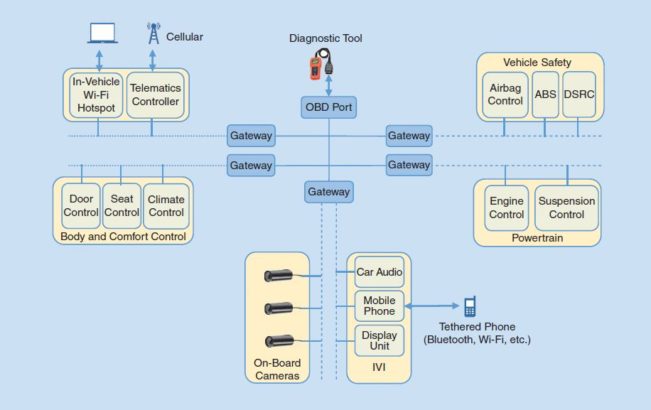
Figure 1: In-Vehicle Network Architecture
Since these subsystems and connection points are interacting with Bluetooth, Wi-Fi, 3G and more, the vehicle becomes accessible from the outside and vulnerable to attacks.
The alarming part is that this only touches on the internal vulnerabilities of vehicles. Beyond the in-vehicle network architecture, cars can be attacked via OBD (On-Board Diagnostic) ports, DSRC (Dedicated Short Range Communications) systems, malware in electronic control unit software updates, and automobile applications like Apple CarPlay.
Because the auto industry can recall vulnerable cars and make adjustments–even though it incurs high costs and reputation damage–they continue to roll out new technologies with limited cybersecurity testing. To address this, Eiza and co-author Qiang Ni identified three available solutions to help prevent vehicle hacking:
- An Over-the-Air Solution: A challenge facing the auto industry is retrofitting protection mechanisms in vehicles that were not secured or need to be secured against a recent threat or vulnerability. To address this, manufacturers have started using over-the-air updates.
While over-the-air updates represent a reasonable solution in response to cyber threats, they are still a security risk. When over-the-air updates are delivered to the connected vehicle, a remote code is needed to execute. Thus, if security is not well implemented around the over-the-air updates, the vehicle is again vulnerable to hacking.
-
- Cloud-Based Solutions: Since it is not feasible to protect each in-vehicle subsystem individually, centralized solutions have emerged as an option for protecting connected vehicles. Cloud-based solutions allow for additional security via encryption and a malware defense framework.Still, there are issues with cloud-based solutions, including delays in routing traffic, general security and the assumption that vehicles are Internet-connected.
- A Layer-Based Solution: The National Highway Traffic Safety Administration (NHTSA) launched a research program that takes a layered approach to cybersecurity. According to the NHTSA, the approach reduces the probability of attacks and mitigates potential ramifications in three ways.
First, preventative measures are implemented such as the isolation of safety-critical subsystems to mitigate the effects of a successful attack. Real-time intrusion detection measures are used for continuous monitoring of potential intrusions in the system. And lastly, real-time response methods are included that aim to preserve the driver’s ability to control the vehicle when an attack is successful.
Although these are potential solutions to hacking, “potential” is the keyword. Eiza believes there is still a long way to go and that more testing is necessary.
Researchers will continue to look for solutions to the weaknesses of connected vehicles, but in the meantime, manufacturers need to adopt more rigorous security assessments. Though there is pressure to keep up with technological advancements in vehicle connectivity, driver safety should still be the top priority.
For more information on connected vehicles, visit the IEEE Xplore Digital Library.





